Recommendation: Map every supplier tier and determine dependencies across regions, then set a 12-week risk-review cadence to pinpoint exposure before disruptions hit.
Step 2: Build real-time visibility by standardizing data feeds; publish content in a common schema, and keep e-mail alerts for deviations; use similar risk profiles to drive applicable actions. Still, ensure cross-functional alignment to translate insights into concrete adjustments in procurement and logistics.
Step 3: Reduce adversarial pressure by diversifying the supplier base, adding 台湾的;台湾人 chip vendors, and preparing a removal plan for single points of failure; monitor exports and regulatory controls on a global 刻度。.
Step 4: Establish a decision-making framework with cross-functional teams, include a rider clause in contracts, and align with parties across the chain to speed response during a disruption; implement a 5-step model for rapid choices.
Step 5: Close the loop with increased performance by tracking exports, demand signals, and supplier capacity; maintain a global view across parties, ensure content updates are shared via dashboards, and set a continuous improvement plan for the next 世纪.
Blue Tiger’s Practical Guide to Exporting and Supply Chain Governance
Begin with a decisive, tiered governance framework that maps every exported product to a control level and assigns clear ownership. Build this framework in software that logs decisions, records approvals, and preserves auditable trails for accountability.
Define export controls, licensing, and documentation requirements for each tier; set access permissions and place a safeguard for sensitive data. Create a standard playbook for entry into markets, including western regions, that guides regulatory checks, logistics coordination, and supplier screen to prevent delays.
Establish ongoing monitoring with real-time dashboards that highlight exceptions and trigger escalation, maintaining keen attention to anomalies. Screen suppliers for compliance and repression risk, applying clear rules regardless of origin. Use governance data to match supplier capabilities with demand signals and pump resources to critical choke points. Maintain the power to adjust or pause shipments when risk thresholds are crossed.
Engage advocacy with customers, trade groups, and regulators to align expectations on safe export practices. Here is a practical plan to coordinate policy, contracts, and training across the network. Choose actions, either through updated contracts or targeted field training.
Strengthening supplier relationships through tiered commitments, transparent scorecards, and proactive risk scoring supports ongoing improvement. Set a cadence to review performance quarterly and by july finalize updates to risk scoring and policy parameters. Focus on ways to reduce risk and ensure exported goods meet demand while staying compliant.
Classify products and shipments to assign correct licenses
Start by mapping each item to a licensing category using named product codes and the end-use profile. Then classify every shipment by destination country-specific conditions and end-users to assign the correct license.
Maintain an annex that hosts the mapping, selected items, and amendments. Keep it current with recent changes; in October, several jurisdictions added rules for offshore equipment and dual-use sensors. Today, use veus from the annex to inform governance and pull insights on topics from reports to reduce ambiguity for fellow team members and end-users alike.
Adopt a two-tier rule: first tag the item with a license code based on its product class; second verify that the recipient and end-use align with the license scope. Tie each shipment to one license in the ERP and attach the record to the line item for traceability.
Key inputs include product category, end-use, and country-specific conditions. For example, deepwater equipment and subsea components typically require licenses tied to controlled technology. Monitor end-users and named recipients; if any persons are not pre-approved, flag for manual review to avoid a violation. Use better screening practices, named-entity checks, and documented amendments to the license file.
insights from recent reviews show that linking license decisions to a country-specific conditions table reduces mis-classifications. The following table translates this rule into concrete steps and demonstrates how selected items map to the license type and required checks. The table aims to help fellow team members know what to apply in day-to-day operations, and it includes notes for end-users.
| Product category | License type | 条件 | 说明 |
|---|---|---|---|
| Deepwater equipment and subsea components | License A (Export Control) | End-users verified; named recipients; US/EU destination restrictions | High-risk category; add to annex |
| Offshore sensing and telemetry devices | License B (Technology License) | End-use restricted; re-export controls; country-specific restrictions | Cross-border transfers require screening |
| Chemicals and solvents for field operations | License C (Chemical License) | Facility screening; end-use checks; compliance with chemical controls | Keep a full amendment history |
| Software and instrumentation for laboratories | License D (Software/Instrumentation License) | User authentication; license keys controlled; country restrictions | Ensure access controls and revocation procedures |
Know the process and use the annex as the single source of truth. The detail you capture today supports faster decisions tomorrow and reduces the risk of non-compliance for end-users and the organization alike.
Map cross-border data flows and implement privacy safeguards
Map cross-border data flows across all parts of your supply chain and implement privacy safeguards immediately. Create a written map to detail data types, recipients, transfer channels, and the jurisdictions involved, from purchasers to service providers, including data embedded in shipments, invoices, or repair logs. Tie the map to your mission and core privacy principles, and align decision-making at the executive level with prior risk considerations as part of privacy practice. Note flows for high-risk items and tag data tied to such materials as gallium for focused protection.
Addressing privacy safeguards begins with embedding checks at each data handoff and applying a risk-based approach to cross-border transfers. Implement data minimization, purpose limitation, and role-based access across core operations. Extend protections to east partners and to other partnerships, codifying security requirements in written contracts with incident reporting and data-retention clauses. Balance controls to avoid arbitrarily restricting legitimate transfers, and embed a privacy practice across all teams to ensure consistency. Noted risks in the map should drive the next controls. Monitor data-flow proliferation and note adjustments in the map, ensuring accountability for every transfer at the senior level.
Establish a quarterly reviewing cadence for the map and privacy controls. Convene a cross-functional team to assess data categories, transfer mechanisms, and incident history, and to adjust the written policy accordingly. As noted in the map, ensure governance covers purchasers, suppliers, and service providers, with ownership at the mission level and checks that close gaps before shipments cross ocean and border lines.
Operationalize by assigning a privacy owner for cross-border flows and embedding privacy into vendor onboarding. Translate the map into a practical set of standard checks and written procedures across procurement, logistics, and IT operations. Require prior due-diligence for new vendors, maintain a live data catalog, and implement incident handling and breach notification tests. Ensure the implemented safeguards align with the mapped risk signals, and keep the data categories, flows, and safeguards up to date through monthly checks and quarterly reviews, with completions noted in the core operations log.
Standardize export documentation and shipment traceability
Adopt a standardized export documentation template and implement real-time shipment traceability across all legs. A match between paperwork and physical movement reduces delays and disputes; this is a serious driver of compliance and customer satisfaction. Pay attention to field definitions and explicitly enforce data quality at every handoff.
- Consolidated data model: create a single schema that covers document type, export license, country of origin, HS code, incoterms, consignee, shipper, notified party, container IDs, bill of lading, packing list items, and event timestamps. Whom approves each field is clearly documented to avoid bottlenecks and confusion.
- Templates and versioning: standardize commercial invoices, packing lists, certificates of origin, and security declarations. Use a centralized repository with version control so changes derive from a defined governance process and are traceable.
- Tiered validation: implement three validation layers (basic completeness, regulatory alignment, and risk screening). Identify several risk indicators and apply criminology-informed patterns to flag suspicious activity, then intensify review for identified high-risk shipments or routes, including chinas suppliers.
- Traceability engine: assign unique shipment IDs and link every event (pickup, departure, handover, customs clearance, arrival) to the consolidated documents. This enables instant response and accurate audits of what was shipped versus what was documented.
- Exception handling and response: define SLAs for document discrepancies, with automated alerts to the responsible team and escalations to whom for legal or regulatory review if needed.
- Exercises and training: run quarterly exercises that simulate document mismatch and clearance delays. Track time to detect, correct, and notify stakeholders, then feed lessons into procedures.
- Governance and onboarding: establish a clear strategy for supplier onboarding with tiered requirements, and specify whether suppliers must meet higher standards for certain routes or customers.
- Communication and expectations: share the standardized definitions, benefits, and responsibilities with all partners. Explicitly state data quality expectations and the consequences of non-conformance.
Finally, establish a concise set of performance metrics: percentage of shipments with fully identified documentation, average reconciliation time, and the number of exceptions resolved within the target response window. The definition of success derives from consistent documentation, improved traceability, and a strengthened response capability, enhancing the overall strategy for global trade and customer trust. We believe adopting this approach will escalate operational discipline, sustaining serious gains across several regions, including chinas, and helping teams focus on continuous improvement.
Vet suppliers for dual-use risk and enforce access controls
Start with a formal supplier vetting process that centers on dual-use risk and enforces access controls at every touchpoint–from inquiry to delivery.
Cross-check every supplier against usml classifications to determine whether offerings are full or part dual-use items and require tighter containment.
Coordinate with like-minded units in marine and civilian sectors to share signals and align risk thresholds; use joint checklists that reflect civilian-use cases and marine operations. Each unit should align controls.
For every event tied to a supplier, verify the origin of orders, confirm received parts against the bill of materials, and review provisions and any supplemental documents that influence risk posture.
Provide a clear appeal path for suppliers to raise concerns, and run quarterly risk reviews at regional hubs such as Queens to ensure detail and transparency. Extend a lighter, interim review channel to queens markets to capture local nuances.
Screen technology suppliers for ties to huaweis ecosystems, and verify that export controls and usml-restricted streams do not impose hidden risk across the supply chain.
Implement unit-level access controls at facilities and warehouses; when credentials do not match roles, the system imposes restrictions and restricts sensitive zones to authorized personnel.
Keep a detailed audit trail of each assessment, recording full reasons for approvals or denials, including whether a supplier covers parts and sub-systems or only provisions.
Engage consulting partners representing customer requirements to strengthen governance; train procurement teams and cross-functional staff, including civilian and like-minded specialists, to raise the bar above baseline expectations and pursue increased resilience.
Track risk events and update case details in the central unit; apply supplemental controls in high-risk cases and ensure all units stay aligned with the program.
Deploy monitoring for regulatory changes amid digital decentralization
Implement a dedicated regulatory intelligence unit and schedule continuous monitoring for updates across key markets. This unit should be staffed by like-minded analysts who have been trained to translate regulatory changes into actionable supply-chain controls. The first step is to establish a three-tier workflow: advisory, actionable, and legally reviewed; each change maps to an updated control owner and a remediation plan.
Pull data from official government portals, regulatory watchdogs, industry associations, and regional publications. Use atlantic market reports to spot cross-border implications and consider offshore jurisdictions for supplier contracts and export controls. Build a registry that addresses compatibility between new rules and existing SOPs. Identify prospective changes early by tracking proposed regulations in july cycles.
Governance: appoint a regulatory lead, schedule weekly updates, and ensure engagement across procurement, manufacturing, and legal. If unsure, escalate to analysts for formal assessment. Here, jake, a compliance analyst, leads the quarterly review with business units to strengthen collaboration with like-minded teams.
Technology and data processing: consolidate feeds in a centralized intelligence hub. Use machine-learning to classify impact by product lines, geography, and supplier risk. Integrate with ERP and S&OP in a modern tech stack to reflect changes in inventory, labeling, and contract terms. Leverage nvidia-based AI acceleration for rapid triage of large regulatory documents. Keep dashboards updated for continuous visibility here.
Measurement and rollout: define targets such as detect within 24 hours, assess within 72 hours, and implement within 15 days for low-to-medium risk changes. Schedule monthly performance reviews; track longer-term improvements and refine the initiative accordingly. Despite decentralization, the program leads to legally compliant operations offshore and onshore, addressing risks in the atlantic and beyond.

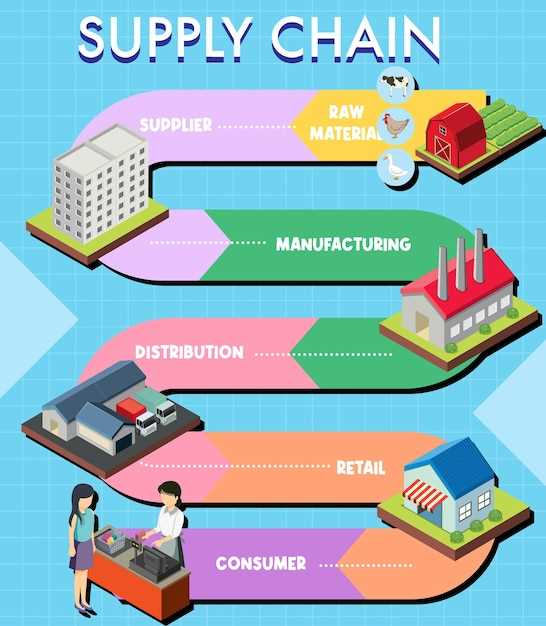
 Five Critical Steps for Supply Chain Management – A Practical Guide">
Five Critical Steps for Supply Chain Management – A Practical Guide">
